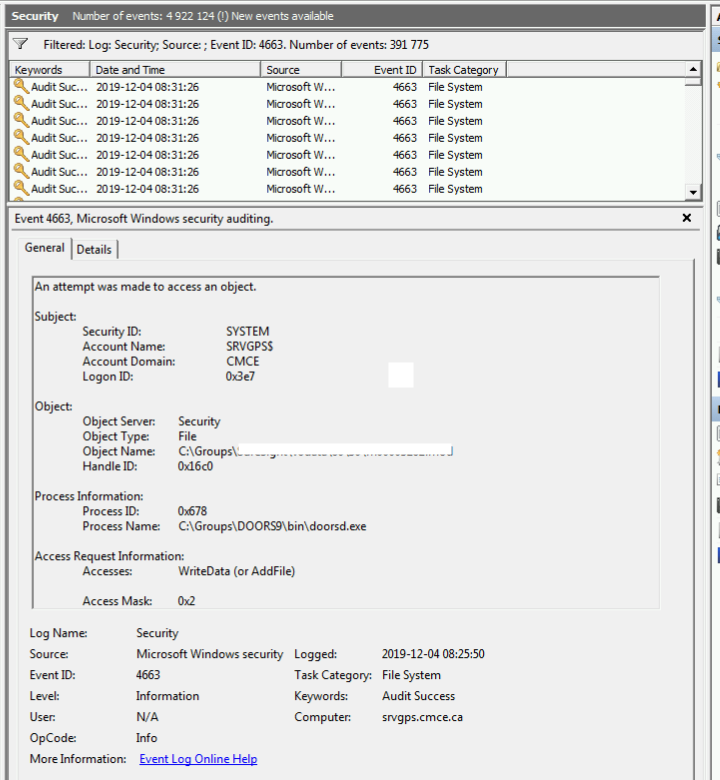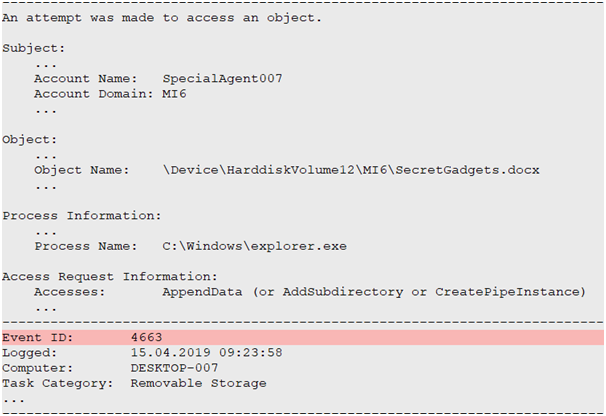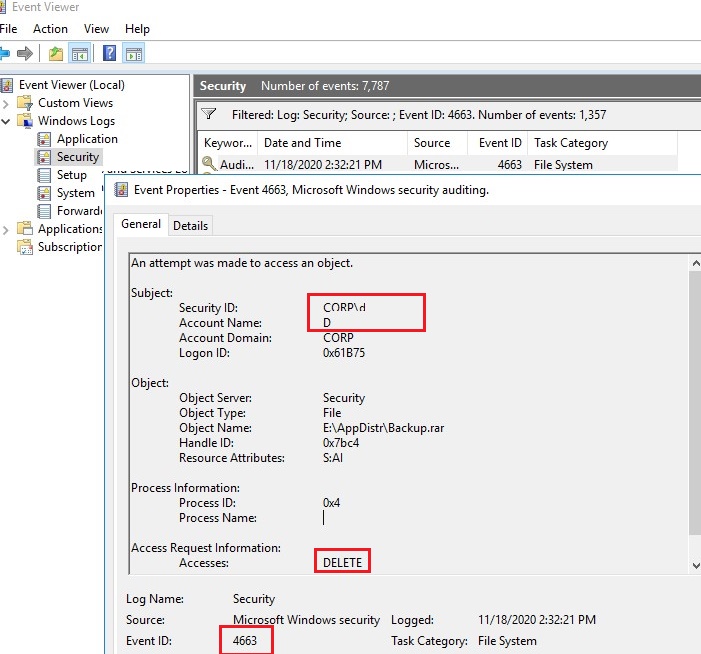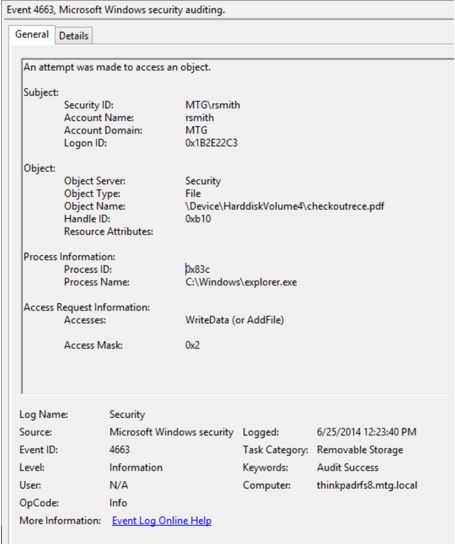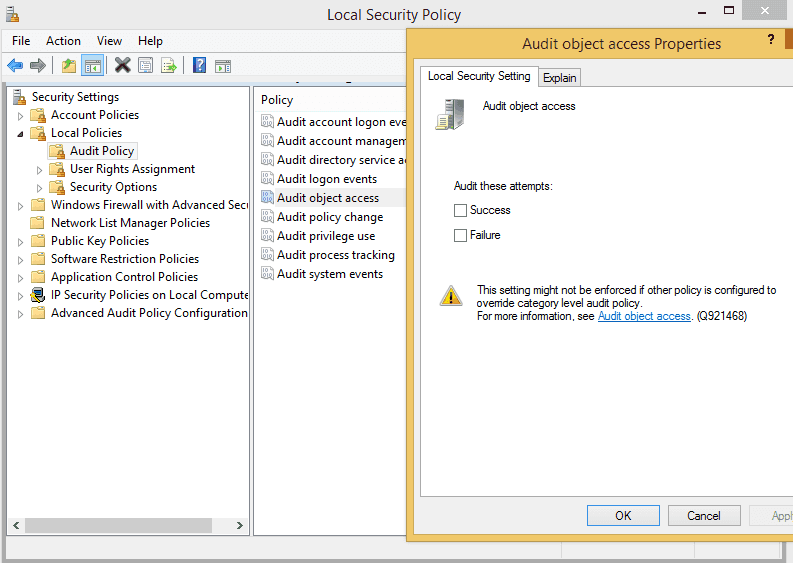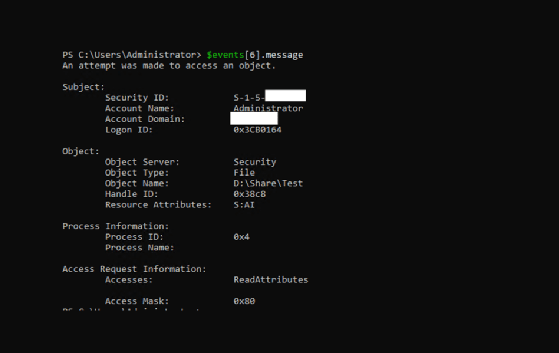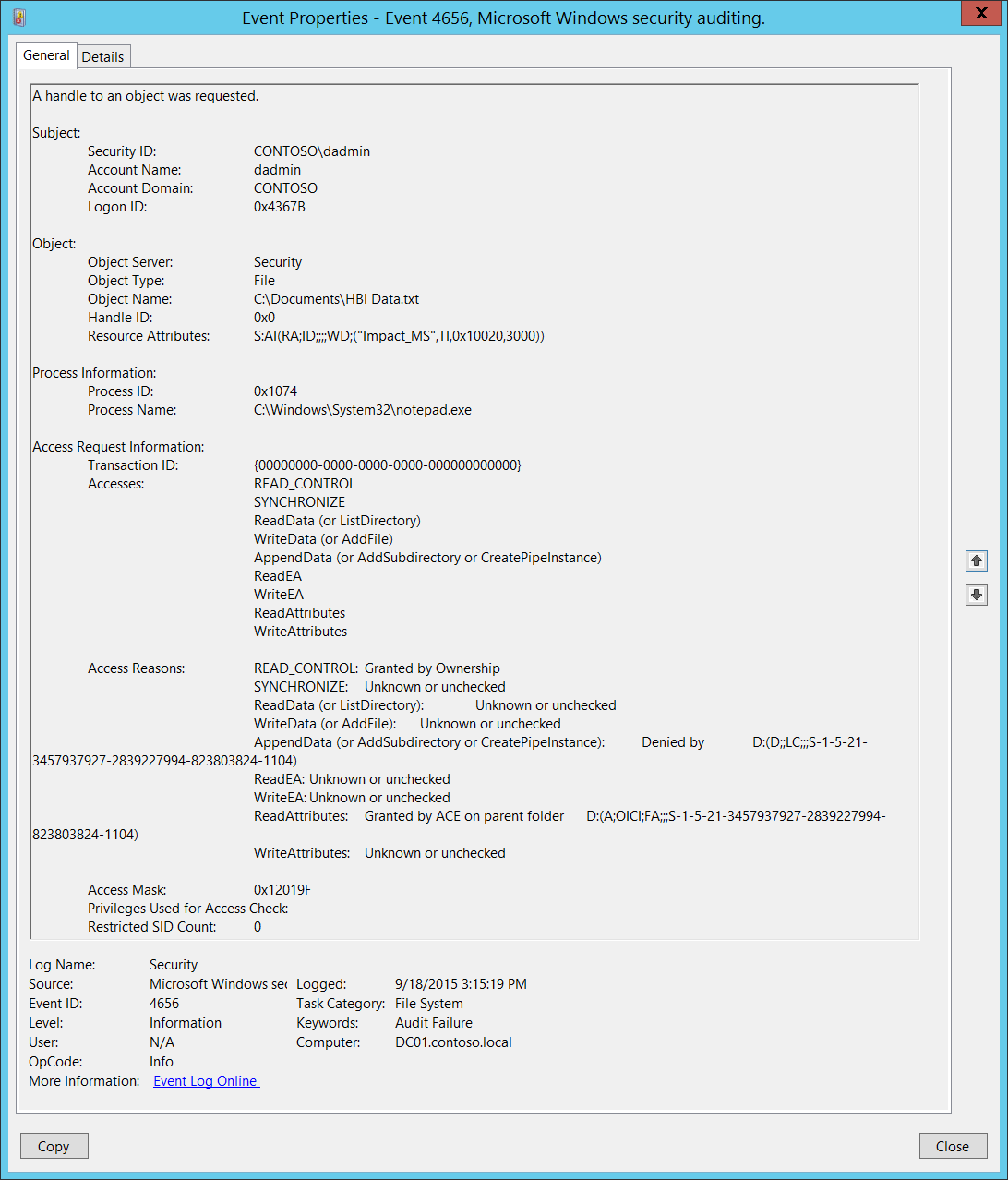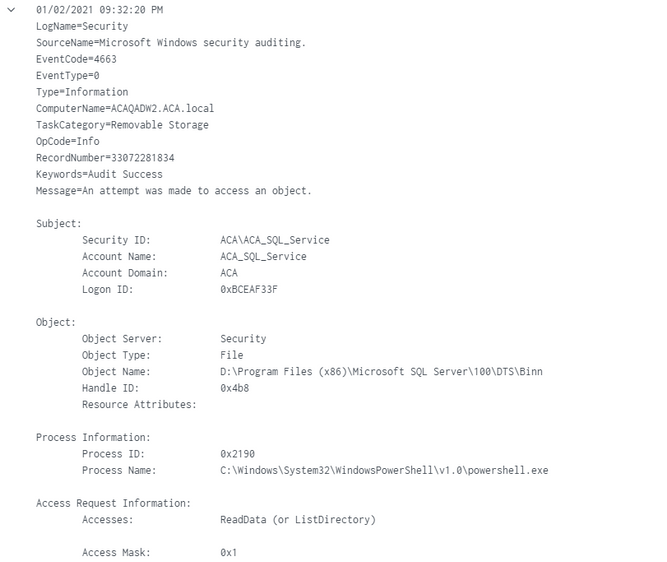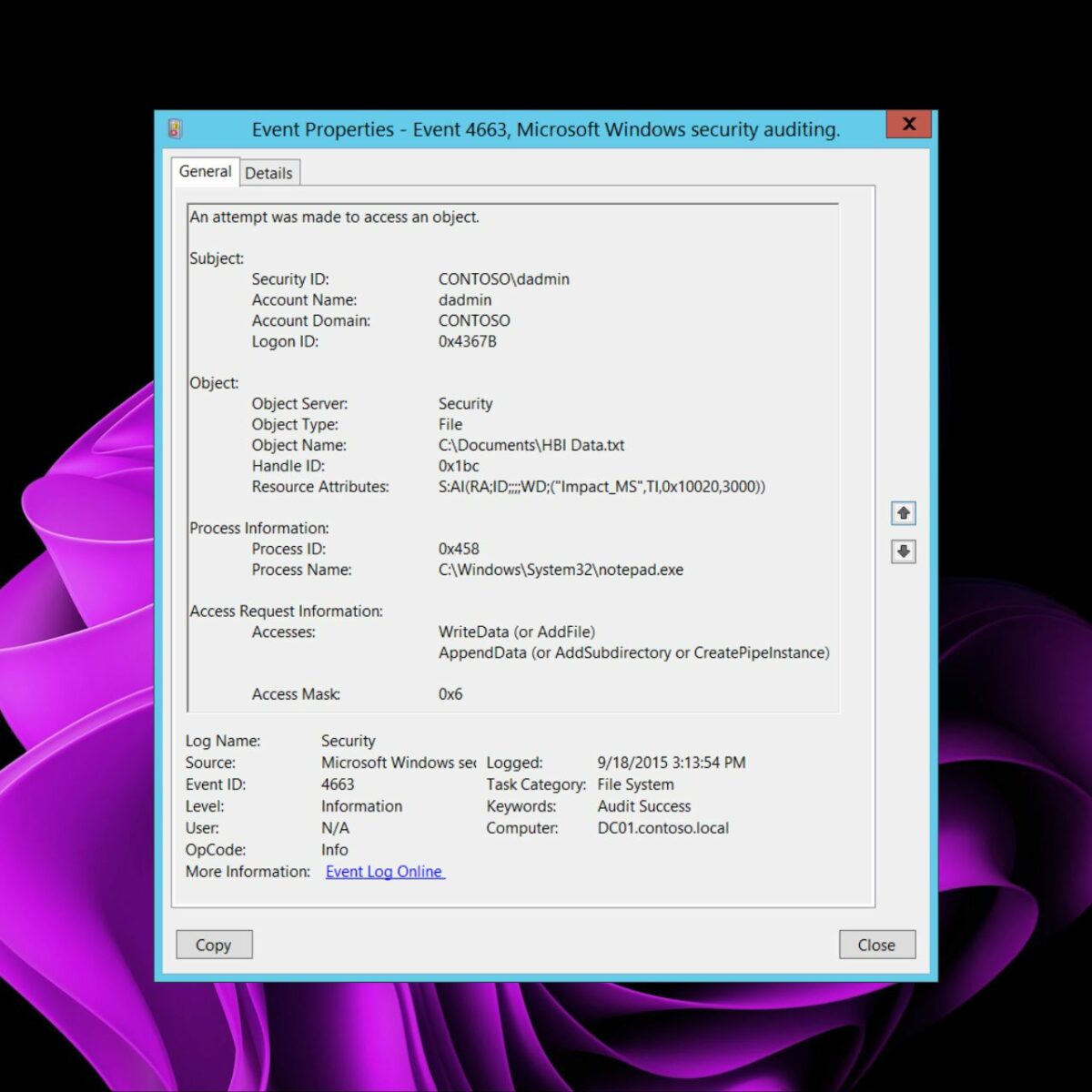
How to audit the windows Event Log for deleted files using event filter in xPath form - Pat Handy Dot COM
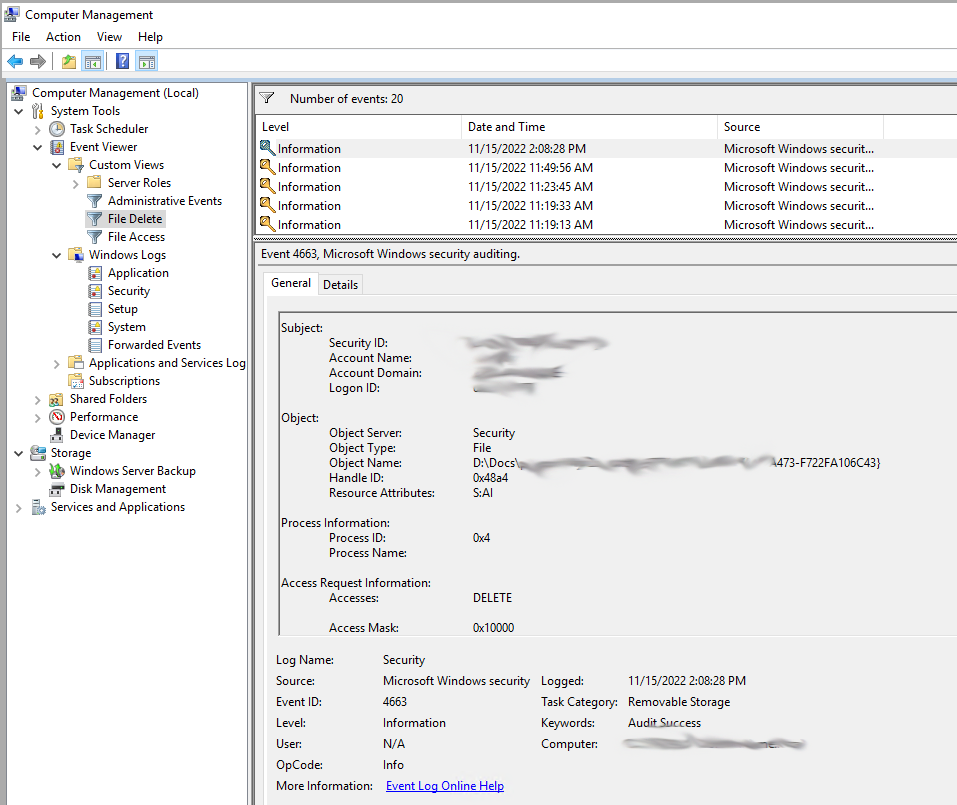
How to audit the windows Event Log for deleted files using event filter in xPath form - Pat Handy Dot COM

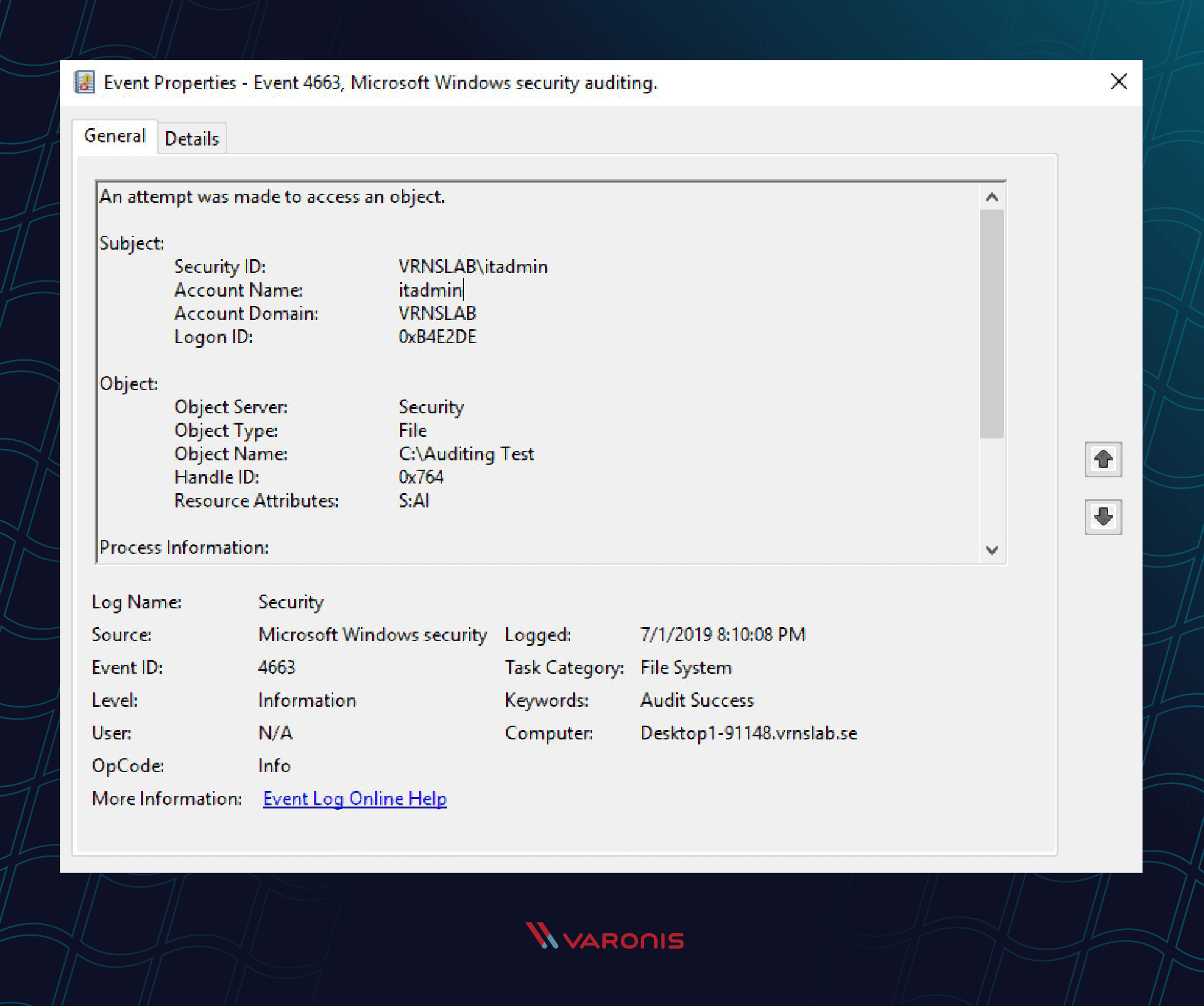
grok Pattern for Event ID 4663 not working extractor - Graylog Central (peer support) - Graylog Community
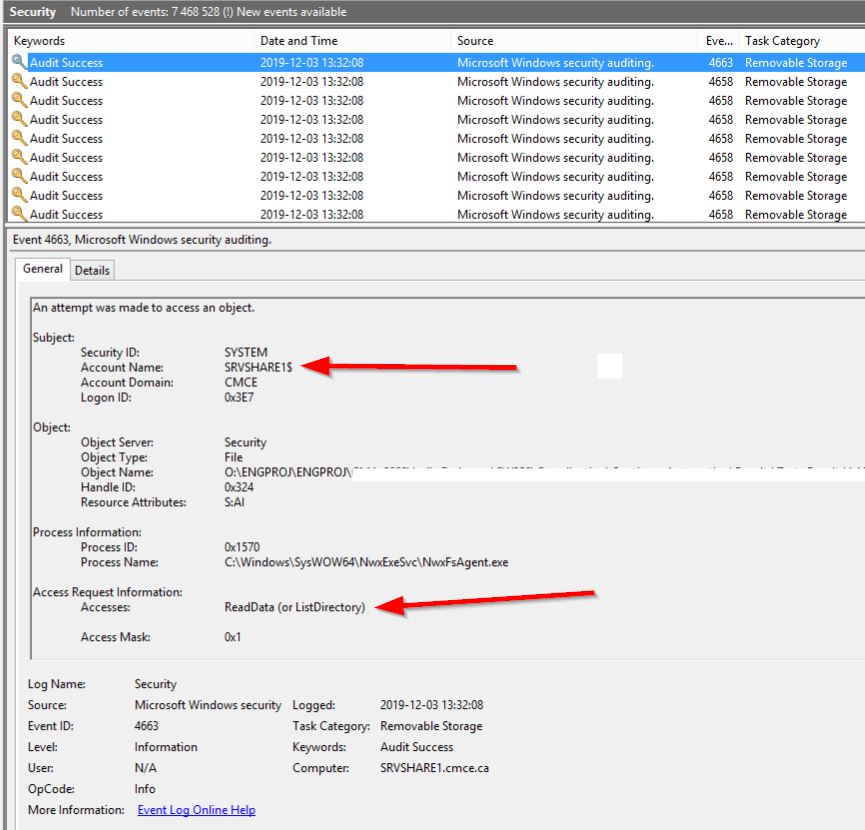
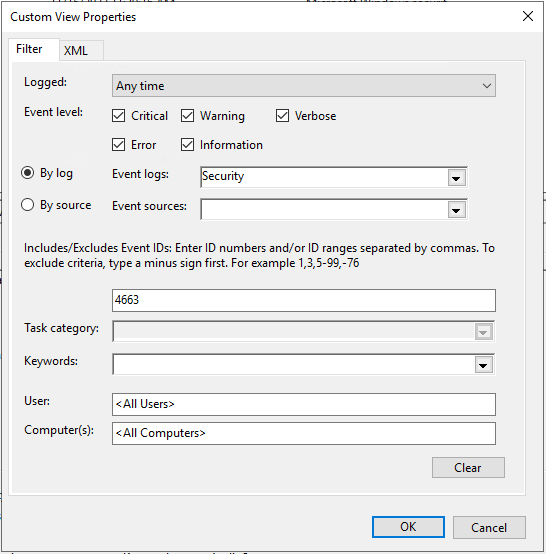
Solved: Too much event id 4663 generated for file access audit on a Windows file server. | Experts Exchange